
An inrtoduction to the ATA drive troubelshooting flowchart from my book, Computer Repair with Diagnostic Flowcharts. This is the first of four drive related …
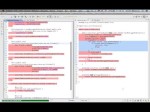
In this video, we take a piece of crappy Java code with no tests. Our objective is to write tests for it and then refactor to make it better. The code has the most common problems that much larger legacy applications have, like Singletons, static calls and feature envy. It also has some design problems. Fixing that is quite hard, mainly when we need to write all the tests before we start the refactoring. Another rule: We cannot change production code if it is not covered by tests but quite often we need to change the production code in order to be able to test it. How to solve this problem? Well, I hope I can answer all these questions in this video. If you want to know more about Software Craftsmanship, please check my book: leanpub.com

CALL THE CMX TEAM HOTLINE: MON-FRI 9AM-8PM EST 1-866-547-7004 Ext. 704 VIEW ALL OPPORTUNITIES VIA MY BLOG: www.BobSolis.com SUBSCRIBE TO MY CHANNEL www.youtube.com DOWNLOAD MY AUDIO BOOK NOW FOR FREE tinyurl.com CONTACT ME THRU MY BLOG: bobsolis.com JOIN ME ON FACEBOOK: tinyurl.com FAIR USE NOTICE: This video may contain copyrighted material. Such material is made available for educational purposes only. This constitutes a ‘fair use’ of any such copyrighted material as provided for in Title 17 USC section 106A -117 of the US Copyright Law.

CALL THE CMX TEAM HOTLINE: MON-FRI 9AM-8PM EST 1-866-547-7004 Ext. 704 VIEW ALL OPPORTUNITIES VIA MY BLOG: www.BobSolis.com SUBSCRIBE TO MY CHANNEL www.youtube.com DOWNLOAD MY AUDIO BOOK NOW FOR FREE tinyurl.com CONTACT ME THRU MY BLOG: bobsolis.com JOIN ME ON FACEBOOK: tinyurl.com FAIR USE NOTICE: This video may contain copyrighted material. Such material is made available for educational purposes only. This constitutes a ‘fair use’ of any such copyrighted material as provided for in Title 17 USC section 106A -117 of the US Copyright Law.

Follow me on twitter: www.twitter.com Like me on Facebook: www.facebook.com Add me to your Google + Circle: gplus.to View my beautiful pictures on Instagram: @BrennanSpark Turn Your Mac into a Wifi Hotspot for your Mobile Devices such as your iPhones, iPads, iPod Touches, and Android Devices Tags: HOW TO TURN YOUR MAC INTO A WIRELESS ROUTER HOW TO TUTORIAL TURN YOUR MAC INTO WIFI HOT SPOT HOTSPOT MOBILE DEVICES IPHONE IPOD TOUCH IPAD APPLE ANDROID DROID IMAC MAC BOOK MACBOOK PRO ETHERNET INTERNET CONNECTION NETWORK HOW TO TURN YOUR COMPUTER INTO A WIFI HOT SPOT ROUTER HOW TO TURN YOUR MAC INTO A WIRELESS ROUTER INTERNET SHARING SYSTEM PREFERENCES BRENNANSTECHBITE BRENNANS TECH BITE

Chris Wysopal, CTO Veracode, Inc discusses valuable insights from his latest book, Art of Software Security Testing, The: Identifying Software Security Flaws.www.informit.com Get all the OnSecurity Vidcasts FREE:www.informit.com Subscribe Now: www.informit.com The Art of Software Security Testing delivers in-depth, up-to-date, battle-tested techniques for anticipating and identifying software security problems before the “bad guys” do. Drawing on decades of experience in application and penetration testing, this book’s authors can help you transform your approach from mere “verification” to proactive “attack.” The authors begin by systematically reviewing the design and coding vulnerabilities that can arise in software, and offering realistic guidance in avoiding them. Next, they show you ways to customize software debugging tools to test the unique aspects of any program and then analyze the results to identify exploitable vulnerabilities. This book is indispensable for every technical professional responsible for software security: testers, QA specialists, security professionals, developers, and more. For IT managers and leaders, it offers a proven blueprint for implementing effective security testing or strengthening existing processes. www.informIT.com/podcasts
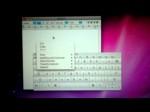
So we thought our macbook was thirsty so we fed it a whole cup of coffee. After paying someone to fix it, it wouldnt even turn on before, we got it back and it sort of works. If I connect an external keyboard and mouse and do not touch the built in trackpad or keyboard, it works fine. But being this is a laptop it would now need to be on a desk. Will replacing the keyboard do it?